Blog
VPN between Friends and Family (VPN Between Houses)
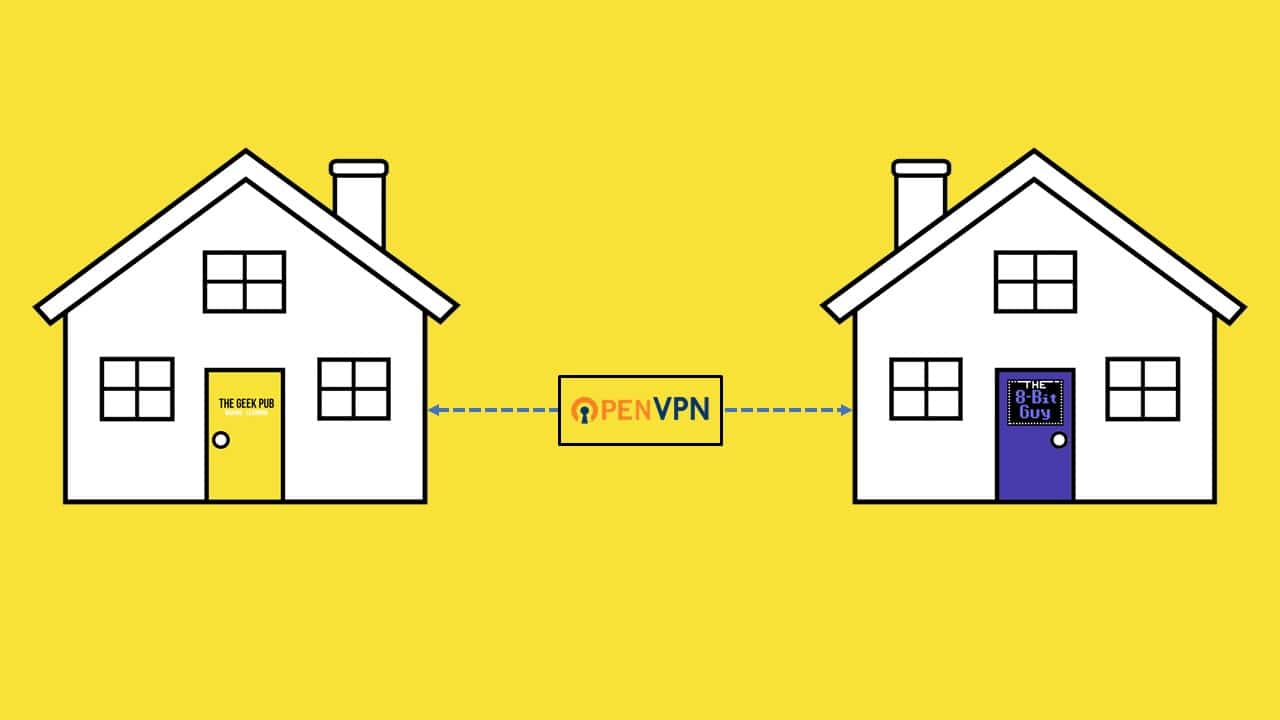
After publishing my updated home network tour article, many of you asked to know more about my firewall setup and all of these VPN connections I mentioned. So in this article we’re going to cover our VPN between friends and family aka, a VPN between houses!
VPN Between Friends and Family Video
Let’s Start with the Firewall
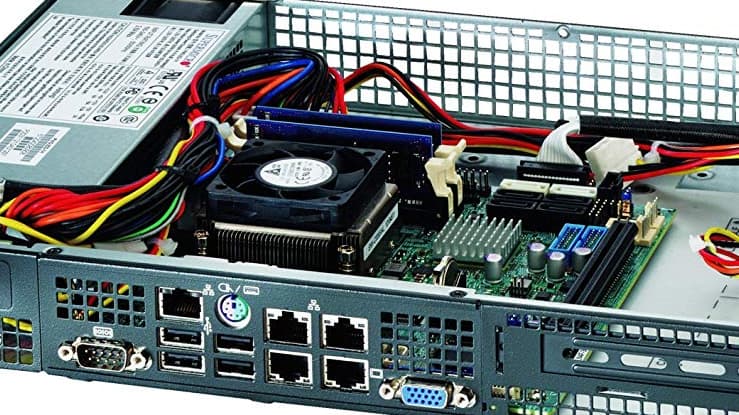
So let’s start with covering my firewall choice and the SuperMicro server that it runs on. I got a lot of questions about this.
The hardware I chose is a SuperMicro 5018D-FN8T. Ultimately, this is nothing more than a Intel Xeon rack server. However, SuperMicro specifically designed it to be used as a firewall or router appliance, hence the 1U small form factor with front facing network ports. The fans are also designed to be reversible to change the airflow direction, giving you numerous mounting options for our VPN between houses!
The appliance also features IPMI management, meaning I can connect to the keyboard/video/mouse remotely over Ethernet even when the box is powered off or even if it crashes. I’ve also populated the firewall’s motherboard with 32GB of RAM and a 500GB NvME drive.
Now being that at the end of the day this is simply a server, you can run anything on here you want. I chose to run pfSense. It’s the worlds most popular Open Source firewall, far surpassing its rivals. With this level of popularity it means a rock solid reliable code base, incredible community support, and lots of 3rd party packages and integrations.
That being said there are plenty of other good choices for a firewall and VPN between friends and family – including OPNSense and Untangle to name a couple.
It might not surprise you then that most of my friends and family also use pfSense for their firewalls. So let’s talk about a VPN between friends and family!
OpenVPN between Friends or Family (aka a VPN between houses)
I have many VPNs up and running, some for remote devices, and some for site-to-site connections. I’m only going to discuss two of them in detail today for brevity, and because I thought they were the most interesting.
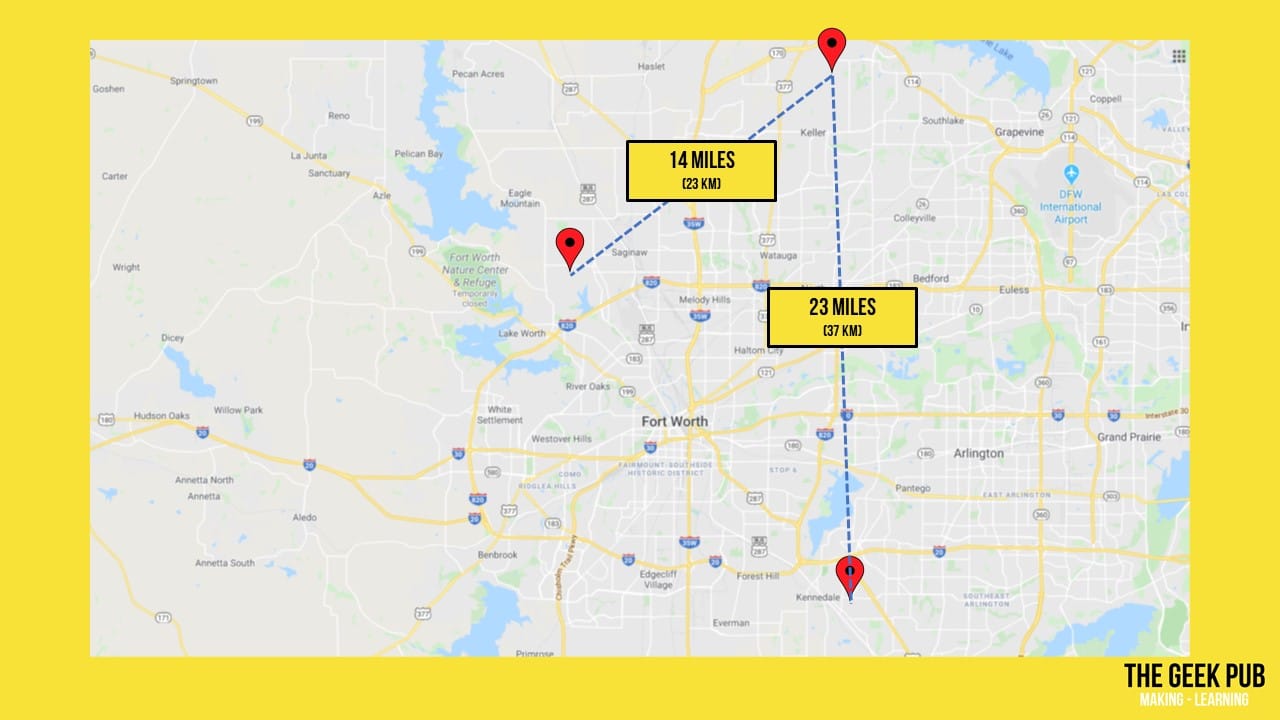
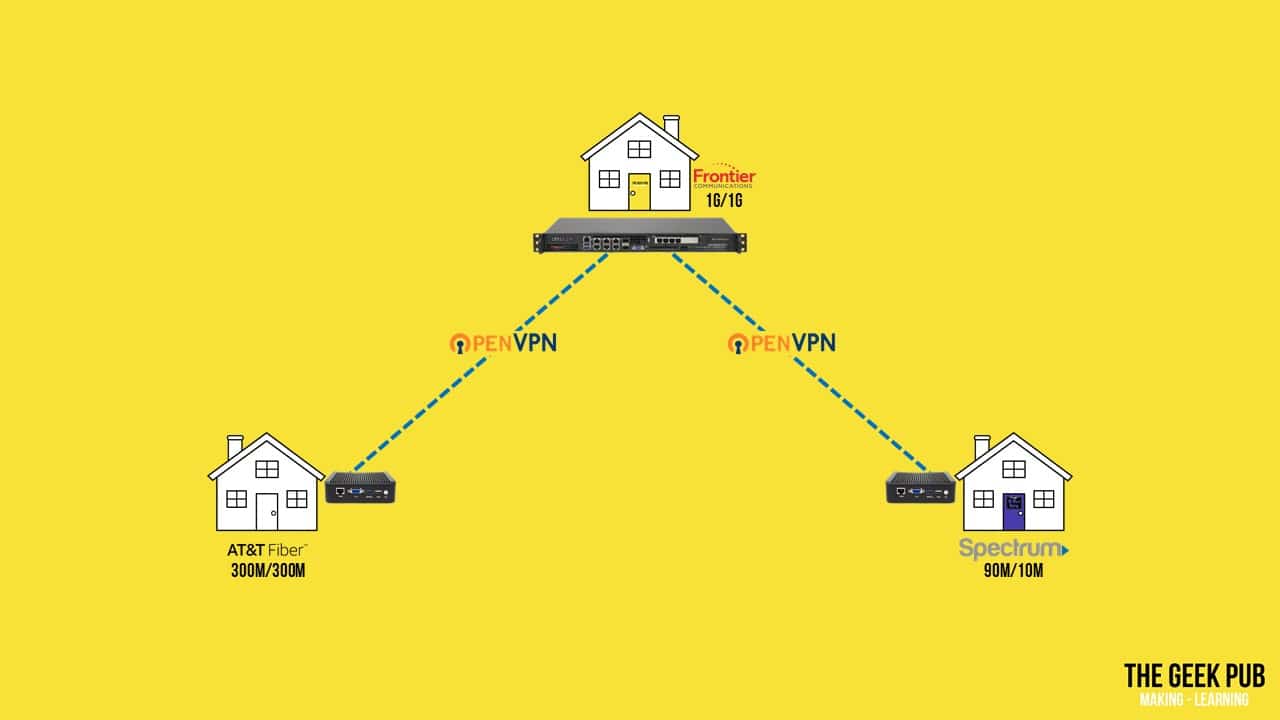
My oldest son, my brother, and I all live in the North Texas area. I live in the northern part of city named Keller. My brother lives in a small town called Kennedale. And my son lives in West Fort Worth. My brother is 23 miles (or 37 kilometers) away as the bird flies, while my son is 14 miles (or 23 kilometers) away.
So let’s stop right here. Some of you are already saying “23 miles away? Why do you need a VPN between houses? You should just use Ubiquiti AirFibers! At that distance you’ll get 1.5 gigabit between you! No need for a VPN between friends and family!”. Well, we actually considered doing just this. And that would have been awesome. Unfortunately it was just not meant to be! If you look at the AirFiber planning map you can see we are link obstructed at both locations do to the terrain between our houses.
So no AirFibers for us. In fact, the only solution that would fix this would be for us to both install towers at our houses and install the AirFibers atop them. However, these towers would have to have been 246 feet (or 75 meters) tall! I don’t think our neighbors or the city would be too happy if were to do this! So VPN it is then!
Luckily, I am in an area where I have symmetrical gigabit services from Frontier Communications. My son’s neighborhood has AT&T Fiber, but he’s only willing to spend enough to get symmetrical 300 megabit service. But poor David being where he lives can only get Spectrum internet at 90 meg down and 10 meg up.
Site to Site VPNs Between Family
As mentioned previously, I have the SuperMicro server as my pfSense box. My son and David both have my favorite Amazon no name boxes for pfSense. These boxes are fanless, while still being quite powerful.
With that all in place, we simply connected the devices using OpenVPN, which is most popular Open Source VPN software on the planet, and is built-in to pfSense out of the box.
OK! So that’s how we’re configure, but what in the world do we do with these tunnels in our VPN between houses?
What Runs over Your Family VPN?
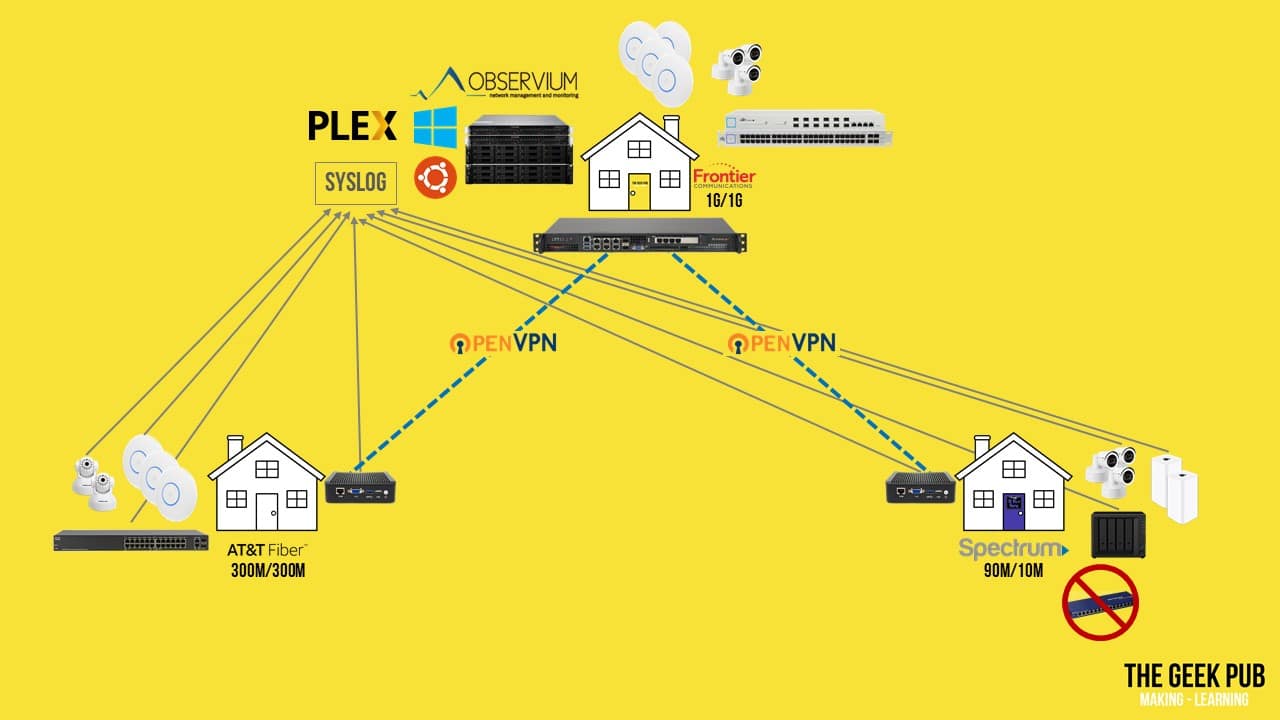
You’ll remember from my recent home network tour that I have two Synology NAS boxes and two SuperMicro 1U servers in my lab. All of this compute and storage can be accessed over the VPN. That means my Son and David both have access to all of my Synology file shares, and any virtual servers I am running.
Of course, PLEX sharing works over the open internet, but in our case PLEX appears to all of our devices as a local service and therefore tunnels over the VPN. This makes PLEX traffic 100% invisible to our ISPs. They can’t shape it, throttle it, or block it.
You might remember from my home network tour video that I also run Observium for system and network monitoring. In addition to monitoring all of my own devices, this box polls SNMP across the VPN tunnels for all of my son’s and David’s devices: tracking uptime, firewall status, bandwidth usage, storage usage, wireless access points, and much more. Well, except for David’s non-enterprise “dumb switches”.
I also run a central Syslog server. Remote devices send their log files here for storage for 90 days. This is super handy for times when things go bump in the night. Not only can we can look back in the logs to see what happened, we can correlate logs across devices to see when one device causes something to go wrong on another. For example, if a camera keeps rebooting, it might be due to the switch running out of power over Ethernet capacity.
And of course, it should be noted that this VPN also works in the opposite direction allowing me to access David’s file shares as well.
What about VPN Network Security?
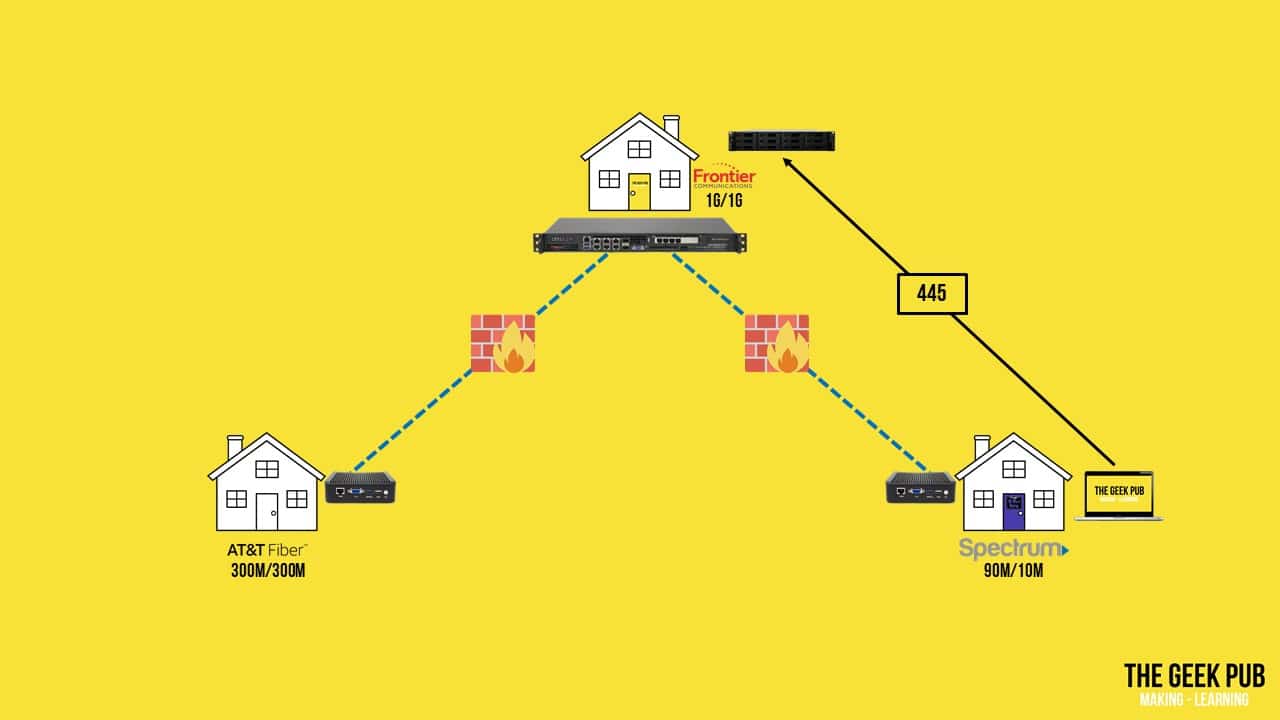
Now, some of you who know networking are probably wondering about security with this VPN between friends and family, and you might be wondering what happens when David gets a virus or some 8-Bit malware on his network. Won’t that just propagate to me?
Well, no. We’re not a bunch of boneheads. These OpenVPN connections have full firewall policies running on them and we only allow very specific traffic across them. This means that only port 445 is open to my NAS for example.
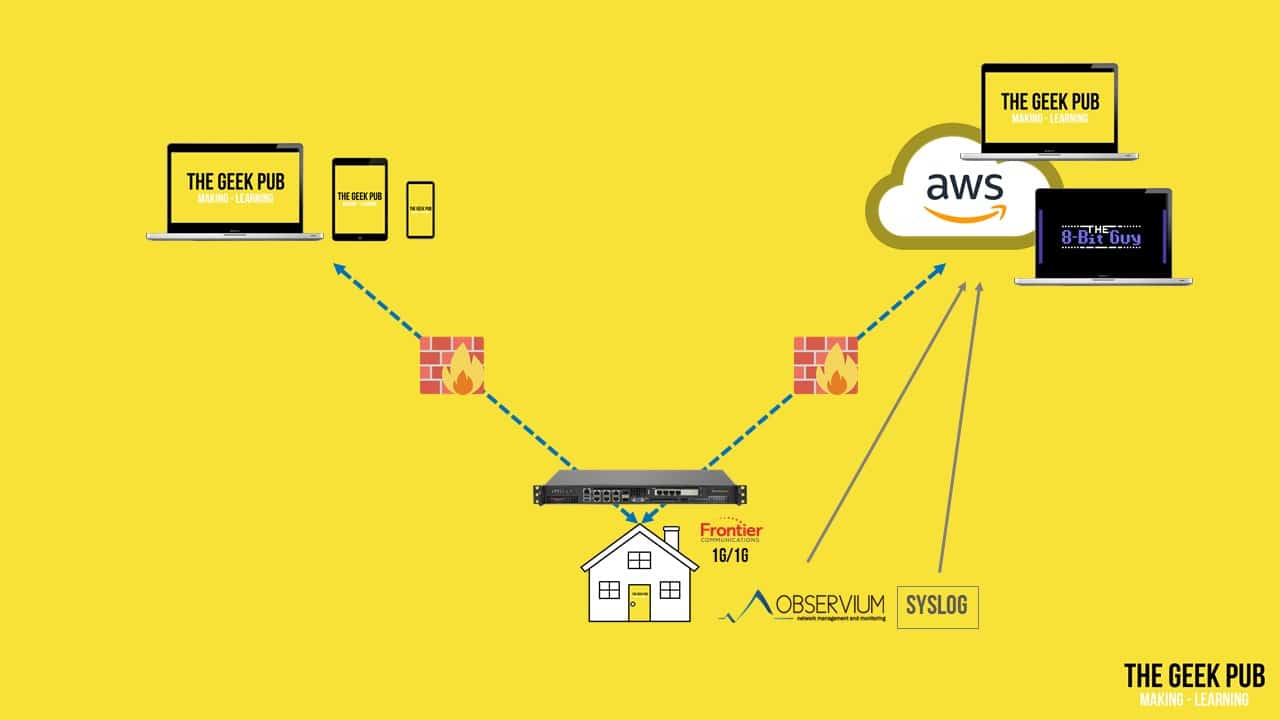
OK. So what other things connect to my VPN? I have a remote access VPN in place so that all of my laptops and phones can connect. In fact, I never access public Wi-Fi without my VPN turned on.
I also have a VPN to my VPC at Amazon Web Services. This is of course where we host TheGeekPub.com and The8BitGuy.com! Remember those Observium and Syslog servers? Those also monitor the health of our webservers. So we immediately know if a server is down, or there is something wrong with it.
If you have any questions about how we use our VPN between friends and family, let me know in the comments below! A VPN between houses can be a lot of fun!












4.5
I really need to do this. This is the motivation I’ve been needing to make it happen.
A bit of a misunderstanding about VPN and being “transparent” here I think; You are still relying on your wan connections here, and it being local traffic as far as the VPN is concerned is irrelevant to that. The ISP is still carrying your VPN traffic. This doesn’t mean it’s invisible to them, but it is encrypted. They can absolutely still throttle and shape that traffic as they wish by prioritizing encrypted traffic lower, or by TCP windowing, or however they choose.
That’s false. Sure, they can shape my VPN as a whole. But they can not shape or see anything inside it. And if they started shaping VPN traffic corporations would abandon those ISPs left and right.
No, it’s not false. They can shape as a whole, and that’s exactly what I was describing. It’s encrypted, so they can’t see what is contained within, but of course they can delay and drop packets as they like. AKA throttling, which is what you were saying couldn’t be done. And ISPs most certainly do shape and prioritize encrypted traffic, and it is something that BPN companies and customers have to contend with. Up until a few years ago, this was very noticeable; A major ISP I won’t mention the name of would see a large decrease In latency of encrypted traffic when you upgrade to a business class circuit. They wouldn’t advertise this, but they would state that VPNs were not supported on their consumer based circuits. Now that VPNs are more popular, that policy has gone the way of the chicken tooth. But to state that ISPs can’t throttle VPN traffic is categorically incorrect. Technically it’s inaccurate, and in practice it happens, plain and simple. And it makes sense if you think about it. Circuits do get saturated, it just happens. How are you going to perform QoS on encrypted traffic, but maintain quality of service for things like Netflix and Spotify and Hulu and Skype and …. I work for just about the largest ISP on the planet, and I can tell you it happens from an experience point of view, and from a technical perspective, I can tell you it doesn’t make sense to say they can’t throttle VPN traffic
@Purple… when you start saying “I can’t name” and “a few years ago” your argument holds a lot less water. Your original comment (and this one) are very poorly worded which is why I suspect Mike didn’t understand what you meant.
To make sure others understand the comment I will try to help clarify. Internet Service Providers can shape and/or throttle your traffic as whole. As long as they are not throttling the VPN protocol then your VPN is immune to it. Mike is also correct that the traffic inside a VPN is invisible to the ISP. They will not be able to tell if you are running PLEX video or a pictures of your kids on that tunnel. Also with that, it is important to mention that in many cases avoiding VPN throttling is as simple as using a non-standard port for your VPN connection. Anyway 99.9% of ISPs do NOT throttle VPN, so this is mostly an edge case not worth anyone’s time to debate.
My argument holds less water because I’m taking measures not to expose myself to legal action. It’s against NDA to discuss some methods and practices of my job, but I didn’t work here when I discovered the very easily provable problem here. I had a VPN to a family member’s house years ago, and we were having issues getting time-sensitive traffic through over the VPN with any quality. We hit roadblocks in support with the ISP not supporting VPNs, and an upgrade to business class service with the same bandwidth dropped latency, though the circuit was technically spec’d the same. This proved out over the years working with several small businesses over the years, as some were small businesses running out of houses on consumer circuits wondering why their VPN traffic was slow, and others on business service had no issue. I’ve experienced it time and time again, and now that I work for a major ISP, I can see why it happens.
I know he’s technically correct to say “traffic within the vpn is invisible,” but the problem is with the wording here; he didn’t say traffic within the vpn, he said vpn traffic, and it’s not invisible, it’s just unreadable. It can still be delayed. I know it sounds like I’m nitpicking here, but these and other details lead to mass confusion regarding VPNs and what they do. People think they make your traffic invisible to everyone, and again they don’t. They make it invisible to everyone except the person terminating your VPN. Unless the traffic is encrypted to begin with of course, but that’s besides the point.
I see what you’re saying about nonstandard ports, but ISPs have been onto that trick for a long while now. They do packet inspection to look at the setup and drop at their discretion. Hotels and schools do this all the time too.
It’s a mistake to assume that 99% of ISPs don’t throttle VPN traffic. Let’s say they’re not throttling it, let’s be generous and say they’re oversubscribed for a second, which to the end user is the same thing because it’s difficult to prove one over the other unless you have a large number of customers cooperating with you. So, in the case the ISP has an oversubscribed node: like you said, VPN traffic is “invisible” (unreadable,) and so they can’t perform QoS, and so you’ll find voice and video over VPN traffic is more often choppy.
Now I know that this is less and less of an issue as time goes on, and major ISPs have been great (lately) about upgrading their infrastructure and keeping oversubscription to a minimum, and thereby reducing motivation for throttling… well that and lawsuits… But, as good as things are now, it still happens. And as fortunate as some of us are to live in or near a city where this is less of an issue, some areas of the US are years behind; ISPs can and do select which traffic to prioritize, and you can guess what they’re going to choose if they have to pick between Netflix that 80% of their customers use, and VPN traffic that maybe 2% of their customers utilize.
My simple point is that stating that VPN traffic “can’t” be throttled is simply untrue, and I think saying that could lead to some further misunderstandings about what VPN is.
@Purple… “I know it sounds like I’m nitpicking here” – Because that’s exactly what you are doing. You knew exactly what he meant, and you just came here to strut your stuff and make yourself feel good in an attempt to act smarter. It’s almost as if you think longer and longer replies make you sound smarter too.
Rob. I edited your comment to remove the harsh language. This a family friendly site. Even if you’re right, you should still be respectful.
What he said was technically incorrect. I pointed out where he was wrong technically. Hopefully it helps clear things up for someone. I don’t care to strut anything, I was just hoping to add to the discussion. If you’re mad at me for having a technical discussion, that’s on you.
Here is the exact quote copied from above. “in our case PLEX appears to all of our devices as a local service and therefore tunnels over the VPN. This makes PLEX traffic 100% invisible to our ISPs. They can’t shape it, throttle it, or block it.” You’ll note I said PLEX traffic inside the tunnel was invisible. I never said VPN traffic was invisible.
Listen, take your evident emotions out of the equations here. Look at the following quote and tell me it’s not potentially misleading for someone who doesn’t have a solid understanding of technology: “They can’t shape it, throttle it, or block it.” I was trying to point out that this isn’t technically accurate. I’m getting resistance here on this simple point. I’m not trying to be a jerk, I’m just trying to add something here. TheGeekPub is an awesome site, I love seeing articles pop up. This one was great too. Perhaps I should have led with that. Again, I’m not trying to be a jerk, I’m trying to add to the discussion.
Sorry Mike. Apologies. I just don’t get guys like this. What you said is absolutely accurate. At this point he’s just arguing for the sake of arguing. I am done here.
I hear you, but they CAN effectively throttle and block it. Having a VPN isn’t a 100% effective way to get around throttling, that’s part of my point here. They can’t block or throttle just the Plex traffic, but they can throttle and block the VPN as a whole. Again, I know you guys are all offended and think I’m just trying to argue here, but I’m trying to help people reading. Taking it personally and saying I’m trying to “strut my stuff” and saying I’m arguing just for the sake of arguing isn’t helping. If you tried to understand what I’m saying, we’d have gotten off on a better foot. Maybe I misunderstood what was being said, maybe you could have added a point of clarity in the article for readers, and all that’s fine. We don’t need to be at each other’s throats in talking about this stuff though. A terse “that’s false” when nothing I said was false, followed by doubling down and going personal doesn’t help anyone.
VPN’s are fun! Why did you choose to go with OpenVPN vs Wireguard? I thought Wireguard would be faster?
It’s built into pfsense and requires no BS to configure.
Hello
OpnSense is a competitor of pfSense (and a fork of the later if I got it right). Some friends of mine adviced me to use OpnSense. Did you study and compared both before using pfSense ? If yes, what made you choose ? Thx…
Do you have any advice for setting up a pfsense device? I have found almost no information online about how to do this from scratch with one of these barebones devices. Do you recommend just buying a device with pfsense preconfigured?
Cool setup, I do however need to comment on your vpn network security section.
Rather than connecting the home networks of your homes to each other I would create an extra network and treat that as untrusted.
At your home you should have your private home network and a separate network for the site-to-site vpn to your brother and son.
Rather than connecting your 3 home networks to each other and and hoping that some port based firewall rules might keep you safe, I recommend a different setup.
Imagine your 3 houses sharing a common garage. You, your brother and your son all have keys to the garage, both only you have a key to your home. So if you want to share stuff with your brother or son you drop it off in the garage and let them get it from there. If your son catches some malware it might burn down his home and the common garage, but it wont affect your home or your brothers home.
So two separate networks at each location with rules like:
Rule 1: Your private home network gets to connect to the internet and to connect to devices in the separate common site-to-site/garage network you run with your brother and son.
Rule 2: Devices on the site-to-site network can only connect to other devices on the site-to-site network, nothing else. It isn’t even allowed onto the internet, only the vpn, and you can’t manage any of the pfsense devices from there.
Each of you put a nas box on the site-to-site network and those nas boxes will be able to connect to each other, but nothing else. As they can’t even get on the internet, the odds of them catching malware or getting hacked is vastly reduced.
Lets say you add a nas box to your private home network too. You put your family photos and videos and what not on that one. That nas box can upload a copy onto your nas box in the “garage”, but the nas box in the “garage” can’t connect to the nas box in your house. Your nas box in the “garage” can then upload to your brothers and your sons nas boxes in the “garage”.
Suffice it to say… I do this stuff for a living and that I am not likely to publish all of the details of how it is designed on the internet, but that we’re not just “connecting your 3 home networks to each other and and hoping that some port based firewall rules might keep you safe”.
No one expects you to reveal all in details, but looking at the number of people that subscribes to your channel and take inspiration from it, it might be wise to sketch out that you’re not just connecting 3 home networks into one. Heck feel free to use my previous post if you like, directly or as an inspiration, it doesn’t reveal any of your network specifics as I don’t know any of your network specifics.
It’s cool that you know what you’re doing and have build something secure, but how about the people taking inspiration from you, do they know that it’s a bad idea to just connect their family networks into one or do they need someone like you to say “Hey it’s a good idea to separate things into different networks for security”??
Hi Mike,
Thanks a lot for this video and also for that one on your network tour, you got me into setting my own pfsense-based infra.
What’s the max throughput your Supermicro firewall can pass via ovpn? Currently, I’ve got 500/30 fiber connection and I wonder what kind of appliance could max it out (currently, I’ve got L2TP tunnel from my Mikrotik 3011 router to a VPS and it reaches maximally 100/30Mbps).
Thanks in advance!
I can get 700mbit or so on a good day. 600 is pretty average.
Purple,
Everything in the post made sense to a networking noob like me. Started reading the comments and found a cluster schmuck of debate over twisted words from a few sentences that were accurate and clearly worded. You’ve taken my attention away from the article and onto you, so who’s the problem here? Clearly you are being disruptive for the sake of of your ego at this point. Please consider other people who just came here for information and reference rather than engaging gross Internet culture toxicity.
Yeah, I’ve also had a similar experience. But since I’m tinkering with VPNs since few years now I’ve got my own thinking and such behaviors are not triggering me anymore 🙂
Thanks a lot for this advice, I’ve replaced my routers with pfSense-based devices (SG5100 in home and pfSense 2.5 on a VPS) and it works much smoother – I’m getting even 490/40 of my 500/30 fiber 🙂
I have a multi-part question/inquiry. After first viewing this video about a year and a half ago, I went and purchased the no-name PFSense box you recommended. I absolutely love it, it was super easy to setup and configure and has been running non-stop (apart from 1 or 2 updates) ever since. So thank you for that recommendation.
I am planning on setting up a 2nd NAS at my parents house using my old Synology DS216j. I just want to have an off sight backup for all my family photos and Plex library. I plan to use Hyper Backup from Synology. I’m already using it for this purpose in my own home, but figured I’d move it off sight as a safer option.
I’m already using OpenVPN on my PFSense box, so I assume I create a new instance of it on the PFSense box and then I can configure it on the DS216J with a new certificate. Then I assume I just leave that connection always active? Or can I setup Hyper Backup to open the connection from my DS920+ to run the backup weekly to my DS216J? I’m thinking this through as I type this….lol.
I don’t plan on getting a 2nd PFSense box for my parents house, I just wanted to connect via OpenVPN through Synology. Do you think that is OK?